Understanding Stressers and DDoS-for-hire Services
Discover the role of stressers in modern network resilience testing.
Stresser Techniques: IP Spoofing
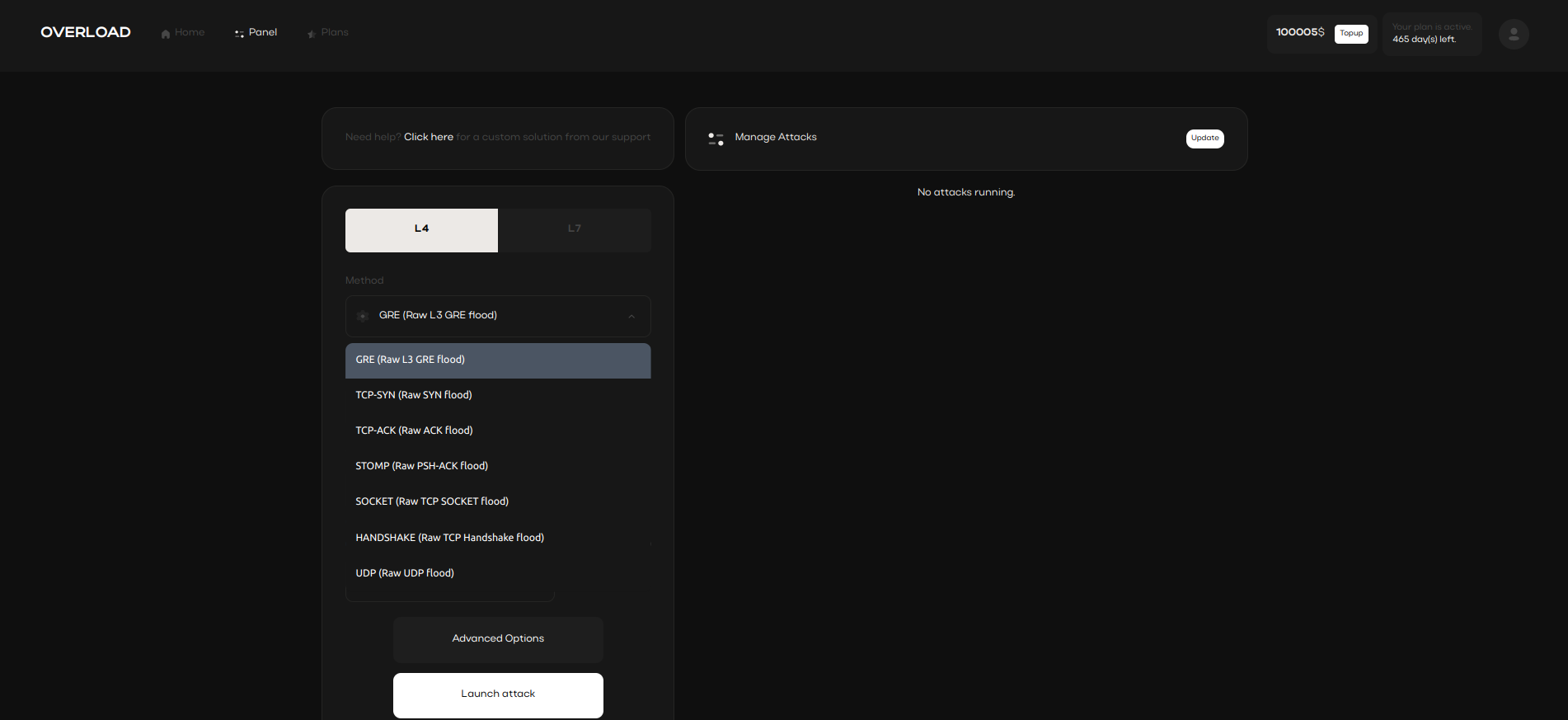
Network Layer 4 (L4) attack methods, commonly utilized in IP stressers, designated specific network protocols to overwhelm servers.
One popular technique is address spoofing, where the attacker’s real IP address is hidden, making it difficult to trace.
These L4 methods and address spoofing tactics are frequently applied to bypass basic network security protections
and effectively simulate high traffic loads on a designated server.
Booters and Their Uses

In addition to stressers, there are also booters
which serve a similar purpose. Booters are often used to simulate high traffic loads and identify security gaps in systems.
These network overload services allow for a exclusive understanding of server durability. However,
misuse of booter services can lead to permitted issues due to unauthorized network attacks.
DNS/NTP/CLDAP Amplification Attacks

source IP obfuscation attacks can be enhanced through various reflection-based techniques, such as DNS, CLDAP, NTP boost.
These methods allow attackers to send small commands and receive significantly larger answers, amplifying the attack’s impact.
By using source IP obfuscation tactics, the attack origin is masked, making it challenging to trace
and prevent the traffic from overwhelming the target’s system.
- DNS reflection method
- NTP amplification
- CLDAP traffic magnification
